There’s a new dangerous group of vulnerabilities that were recently discovered to be impacting all devices that use Wi-Fi. These vulnerabilities have been around since before 2000 but were only recently discovered.
watch a short video > https://youtu.be/kdrJRhilgB4
The vulnerabilities are collectively called Fragmentation and Aggregation Attacks, FragAttacks for short. These impact just about every device you have, including computers, smartphones, tablets, and IoT devices.
FragAttacks are a collection of weaknesses in the Wi-Fi 802.11 standard design and programming mistakes in Wi-Fi products themselves. It’s estimated that every Wi-Fi-enabled device is impacted by at least one of these vulnerabilities, but most are impacted by more than one.
The vulnerabilities allow radio signals from your router or Wi-Fi hotspot to be used to exploit the devices for a variety of reasons. If you don’t have any type of protection or remote support for those devices you could be vulnerable to an attack.
What Do These FragAttacks Do?
Depending upon the attack and vulnerabilities being exploited, an attacker can do several things. FragAttacks allow hackers an entry into a device and from there, they can:
- Inject the device with malware
- Steal sensitive data the device contains
- Take control over the device
- Inject an unencrypted Wi-Fi frame into a network (leaving data exposed)
- Intercept traffic meant for the device
- Bypass the NAT/firewall in a router
- Send unencrypted broadcast fragments that devices will accept (these can be malicious code)
- Cause a Wi-Fi to keep the memory of a connected user’s data transmissions and read those even after the user has disconnected
If these flaws have existed for over two decades, why haven’t we heard about them until now?
The flaws aren’t easy to manipulate and as the Wi-Fi security protocol Wi-Fi Protected Access (WPA) has evolved, security issues were thought to be addressed along the way. The growth of IoT devices and the use of Wi-Fi provided the volume of data needed for researchers to identify and shed light upon FragAttacks.
Another reason that FragAttacks hadn’t been discovered before, is that there has yet to be evidence of any widespread attacks exploiting these flaws. Some require enough physical presence near the device, that they aren’t much good to a hacker halfway across the world. But they are very concerning anytime you’re using public Wi-Fi where anyone could be connected.
What Can You Do to Mitigate FragAttacks on Your Devices?
Keep All Your Device Firmware & Software Updated
It’s vital to keep all your devices patched and updated regularly. Some manufacturers have already sent out patches to address FragAttacks vulnerabilities, but if users don’t install those updates, then they don’t do much good.
Firmware updates are often forgotten about by users, especially for equipment like routers that get set up and left alone unless there’s an outage. Users often don’t go back into their router settings regularly to check for any needed updates.
Putting your Hamilton County business on a managed IT services plan can ensure that all devices are being properly updated for the operating system, software, and firmware patches.
Only Visit Websites Using HTTPS
FragAttacks use unencrypted protocols to steal user data, so by staying on websites that use HTTPS (the “S” is for security) instead of just HTTP, you can protect yourself from these attacks.
HTTPS uses a security protocol that encrypts all website traffic and any data you send to the site (contact form, credit card, etc.). Encryption secures the data so a hacker can’t intercept and read it.
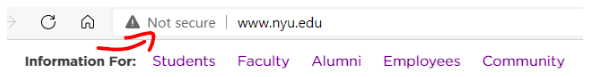
Pay attention to the address bar whenever visiting a website. Your browser should indicate when you’re on a site that doesn’t use encryption and you’ll see a “Not secure” or similar designation. This is an indication that you should leave the site or be very careful about entering any data into a form because the information you send could be compromised using FragAttacks.
Use a VPN on Any Public Network
When on any public Wi-Fi network, you should use a reliable VPN (Virtual Private Network). This is a low-cost service that allows you to connect to secure VPN servers that encrypt your traffic.
VPNs can be used on PCs and mobile devices and will allow your traffic to remain encrypted even if you’re on unsecured public Wi-Fi. VPNs are also a good idea when traveling and for any remote employees that you have working from home.
Is Your Device Firmware Properly Updated?
Magnify247 can help your Hamilton County business avoid attacks on your Wi-Fi devices through a patch and update management plan and other safeguards.







