Many online services allow users to reset their passwords by clicking a link sent via SMS, and this widespread practice has turned mobile phone numbers into de facto identity documents. Which means losing control over one thanks to a divorce, job termination, or financial crisis can be devastating.
watch short video > https://youtu.be/ztM5lBnF6l4
Even so, plenty of people willingly abandon a mobile number without considering the potential fallout to their digital identities when those digits invariably get reassigned to someone else. New research shows how fraudsters can abuse wireless provider websites to identify available, recycled mobile numbers that allow password resets at a range of email providers and financial services online.
Just think about all the personal information that you receive via SMS on to your mobile number:
- Shipment delivery notifications
- Multi-factor authentication codes
- Password resets notices
- Medical appointment confirmations
- Payment confirmations
- Bank notice about potentially fraudulent transactions
- And more
That type of information being in the wrong hands can lead to serious cybersecurity issues and potential identity theft. So, changing your mobile phone number can have a much bigger impact than just having to give your friends and family a new number to reach you.
Princeton University Study
The fact that we tie our phone numbers to so much personal data is a newer phenomenon that has happened along with the rise of smartphones. When phones were only used for making and receiving calls, it wasn’t such as big security risk when you changed your phone number.
But we have so many digital footprints out there now that are tied to our mobile number, that changing or losing your number can have widespread consequences.
There was a recent study done by Princeton University on the risks of recycling a mobile phone number.
The study looked at 259 mobile numbers that were available to be used by new subscribers at two major phone carriers and found that 66% of them (171) were connected to accounts held with popular websites.
All an unscrupulous hacker would need to do is attempt a login and use the mobile number to hijack that account. If it’s an account like Amazon that might have a credit card stored in the online wallet, it could do a lot of damage.
Further, researchers were able to do online searches on those available numbers and find personally identifiable information on the former owners of the cell numbers.
If that’s not enough to make you want to hang onto your mobile number as well as question the one you may be issued when signing up for a new service, another finding by the researchers was related to leaked login credentials.
They found that 100 of the 259 available mobile numbers were linked to login credentials that had been leaked online. So, with the combination of login credentials and the phone to receive the MFA code by SMS, it would be simple for a thief to log into all kinds of accounts attached to a mobile phone number that someone abandoned.
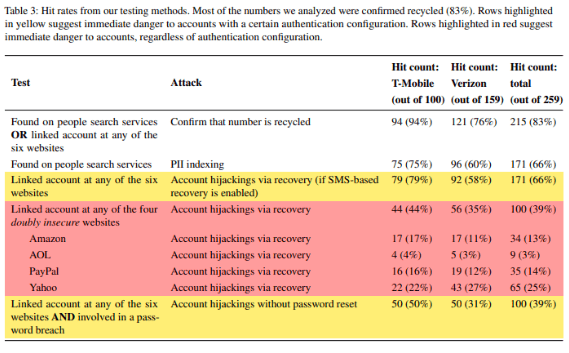
Data from Princeton University Study
What Hackers Can Do With This Knowledge
The fact that recycled phone numbers can unlock online accounts and other personal data related to the former owner is not lost on criminals.
In fact, they will browse numbers made available to customers interested in signing up for a prepaid account at services like T-Mobile and Verizon. They’ll ignore blocks of consecutive numbers, which indicate these are new and not recycled. Instead, they will zero in on the random numbers that most likely had former owners. They can then use these for phishing, vishing, and other types of attacks.
Some of the attacks that someone can deploy by obtaining a recycled mobile number include:
- PII Indexing: Hackers review the list of the available numbers on a carrier site and do a web search to see which ones bring up the most personally identifiable information (PII), then they obtain those numbers. Scammers can then phish the previous owner’s friends and family among other things.
- Account Hijackings: Attackers can use both password recovery and multi-factor authentication, depending upon what’s been set up on an account attached to that number, to log in to an online account as the phone number’s former owner.
- Targeted Takeovers: With everyone sharing their day-to-day personal business (new job, where they had lunch, vacation timing, etc.) over social media, it’s not that difficult for a criminal to know when an acquaintance’s number may have changed because they may post about it on their social feed. They can then look to obtain that number when available.
The bottom line is that you want to think hard before abandoning your mobile number. And if you must change the number, go through the process of disconnecting that number from all your online accounts and any MFA and password reset processes.
Keep Your Devices & Data Protected With Help from Magnify247
Magnify247 can help your Hamilton County home or business put protections and best practices in place that keep you better protected against multiple online threats.
Contact us today to learn more!







