When creating an incident response plan, the detection and response stages are critical components. It is important to know how to detect when an incident occurs and the appropriate response to help mitigate the damage.
watch short video > https://youtu.be/Y_nIOCTvMMQ
In part two of this three-part series, learn some important steps to help detect and respond to security incidents promptly.
The clock is ticking when it comes to an IT security incident. Worms, ransomware, and other types of malware are quickly scanning an infected device for any signs of connections to other data. The malicious code seeks out any network connections it can use to reach other devices using the same Wi-Fi. It also looks for syncing backups or cloud storage applications.
The faster you detect and respond to a breach, the more you mitigate your costs.
The average savings from containing a data breach in less than 200 days versus over 200 days is $1 million.
In part 1 of our series on creating a great incident response plan, we discussed preparation activities. Now we’re getting into the nitty-gritty of how to identify threats and respond to them swiftly.
Tips for Detection & Response for Cyber Incidents
Protect Your Device with Antivirus/Anti-Malware & OS Security
One of the best ways to detect intrusions into your PC is through the use of security applications. This includes using a reliable antivirus/anti-malware application and deploying the features you have available in Windows 10 or another operating system.
For example, you can turn on features like Ransomware Protection in the Security Settings of Windows 10 to protect files and folders from malicious programs.
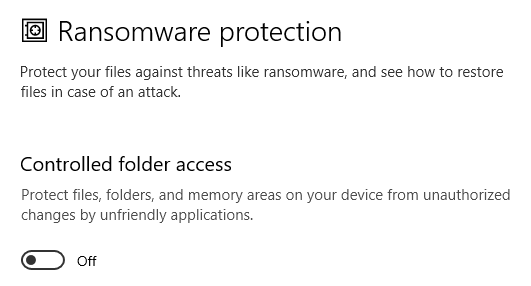
Windows 10 Ransomware Protection Setting
Stay Alert for Warning Signs
Some attacks have very visible signs, such as a ransomware note on your screen and the inability to access any of your files.
But some, like spyware, are designed to fly under the radar and infiltrate your device undetected by the user.
It’s important to stay alert for any warning signs that could point to malware infection of some kind on both your work and home computers. Some of these are:
- You find your applications crashing and being problematic
- Your hard drive space is being depleted quickly
- Strange system warnings start to appear
- Your computer slows down considerably
- Your home page in your browser has been changed
Don’t Panic & Contact Your Team
Don’t panic if an incident occurs; stick to your plan and work with your team. Often, the first response is to be unsure what to do and to panic and start clicking all the wrong things or to freeze and not do anything. Both of those responses can cause the matter to get worse.
The point of the preparation stage in your incident response planning is to put together a “go-to” team that you can rely on and go to for help should you detect any potential breach or malware infection.
Know who to contact:
- Work device: Contact your IT department or IT professional
- Home device: Contact the cybersecurity “help team” you’ve put together in Step 1.
Knowing who to contact speeds up your response and alleviates that panicked feeling.
Unplug Your Device from the Internet
Malware can spread rapidly through a network, so the first thing you want to do if you suspect an infection is to disconnect your device from the internet and any internal network that may be using ethernet cables.
This isolates your machine and stops it from infecting others on the same network.
Start Device in Safe Mode
Try restarting your device in “safe mode” to help troubleshoot issues safely. Safe mode only loads certain critical programs and greatly reduces the chance of further exploitation by the malicious code.
Use Another Device to Research the Issue
A key mistake many people make when they think they have a virus or malware infection on their PC is to go to their browser on that device to research it. This means that they haven’t disconnected their computer from the internet, so other devices may be getting infected.
After disconnecting your device and restarting it in Safe mode, use a different device to research the issue online to see if you can find any clues that may help.
Get IT Help If You Can’t Fix the Problem
If you and your team are not able to eliminate the threat or stop the strange computer behavior, then it’s best to have a computer professional, like Magnify247, take a look at your system and safely remove the threat.
Paste this URL into your browser to learn more: https://www.pii-protect.com/MicroTrainings/micro_training_view/212?brand_key=dahfx&ID=478345
Improve Your Device Protection With Help from the Pros
Magnify247 can help your Hamilton County business and your employees with a fast response to any cybersecurity incident to mitigate the cost and risk to other devices.
Contact us today to learn more!







